Data breaches and cyberattacks are becoming increasingly common, with a staggering 85% of such incidents being financially motivated. These threats target companies’ financial data, intellectual property, health records, and, most critically, customer identities, which are then sold on the dark web.
Around 70% of these breaches are perpetrated by external actors, making endpoint detection and security a crucial aspect of cybersecurity. These actors can be part of organized crime syndicates or individuals operating from remote locations.
Verizon’s Data Breach Report highlights the grim reality of cyber threats and underscores the importance of preparedness. A particularly alarming statistic is that these cybercriminals are well-funded and actively seek out unprotected endpoints.
Why Are Cyber Threats So Alarming for Enterprises?
The lack of rigor in asset management is creating new and unforeseen threats, as companies often fail to assess the current health of their infrastructure. For some companies, asset management can be as complex as the Mariana Trench in the Pacific, leading to partial or no protection against threats.
According to the same report, nearly 24% of these threats or breaches involve cloud assets. Information security officers and EDR implementation experts agree that the most valuable lesson they learned during the pandemic was the need to accelerate cloud migration. While cloud migration enhances workforce productivity, it also exposes companies to higher risk levels. Today’s cybersecurity landscape calls for CISOs to prioritize on-premises cloud SIEM (Security Information and Event Management) and security applications. The future of cybersecurity hinges on cloud-based endpoints and the applications they support, as most enterprises are shifting their work environments to the cloud.

Over 60% of hacking-related breaches involve brute force attacks or stolen credentials. The Verizon report emphasizes the importance of protecting personal access credentials. By keeping endpoint software updated, monitoring activity levels, and promptly addressing configuration changes, companies can significantly reduce the risk of breaches and potential damage to their proprietary assets and compliance.
The Path Forward: Enhancing Cybersecurity
To effectively combat cyber threats, enterprises need access to more insightful analytical data on the health of each system deployed and integrated into their infrastructure. While multiple dashboards can provide this data, EDR solutions tailored to specific business requirements offer enhanced scalability and adaptability.
Looking ahead, autonomous endpoints capable of self-assessment, OS regeneration, and configuration will play a pivotal role in shaping the future of cybersecurity. While companies focus on cost optimization, information security officers must prioritize anticipating and protecting the enterprise from these stealth-level breaches.
By bridging the gaps in asset management and securing every endpoint, enterprises can establish a secure and uninterrupted business environment.
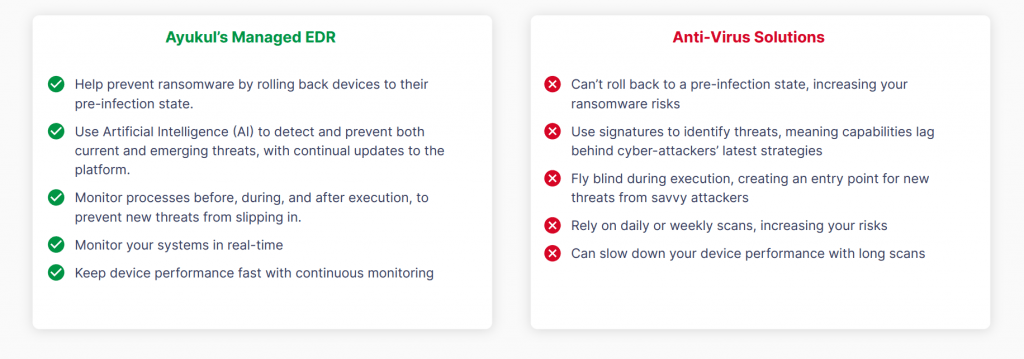
To understand the difference between a secured Endpoint solution and an Anti-Virus, here is a table that we can go through: